Hello 3C and Capital City Dental Clients,
- Crypto Ransomware Attacks on the rise: We have seen a huge increase in phishing email attacks. In most cases the victim is tricked into clicking on a bad attachment and launches the attack. If you don’t have Locker Watcher installed on your server and/or you haven’t sent your employees through our cybersecurity class, you are at HIGH RISK! All users SHOULD BE ON HIGH ALERT! THINK BEFORE YOU CLICK!
- RDP Accounts are being Brute Forced: If you are still using RDP for remote access, you are at HIGH RISK! We have seen numerous RDP brute force attacks on networks with RDP in use. Please consider upgrading your remote connection methods to Casper, or VPN, which are much safer than RDP.
- Dridex Banking Trojan Infections on the Rise: We are seeing many infections with the Dridex banking trojan. If you still have a Windows XP machine anywhere in the office or at home, Dridex is GOING TO LOVE YOU! This trojan tries to spread to all computers on the infected network using software exploits or weak/common passwords. If it successfully infects every machine on the network, it is very hard to remove. Once installed, it will send phishing emails to everyone in the outlook contacts of infected machines and also tries to steal banking access information using key loggers. The phishing emails pretend to deliver an invoice to the recipient and opening the invoice will launch the virus. See below for examples of real phishing invoice emails we have quarantined:
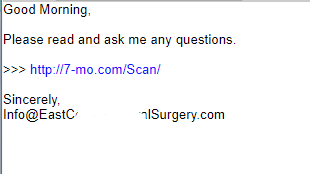
Example #1 – This attack pretended to be from a local company but actually came from Denmark!
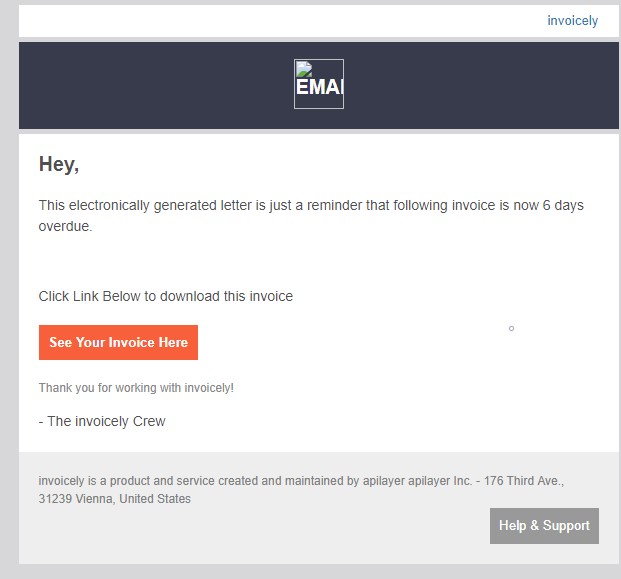
Example #2 – This email pretends to be from “invoicely”, a popular invoicing service.
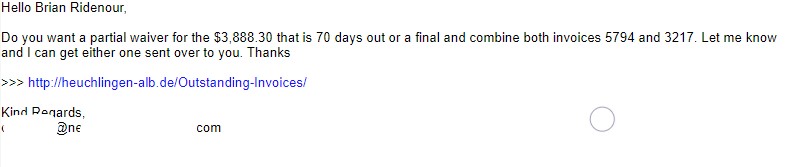
Example #3 – This one was directed at 3C and appeared to come from one of our clients.
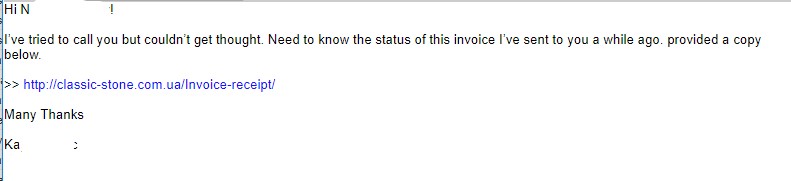
Example #4 – This phishing email appeared to be from one employee to another employee within the same company!
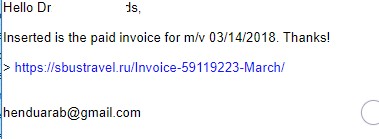
Example #5 – This phishing email is using a fake gmail account hoping the doctor will think it is a patient.
BREAK/FIX CLIENTS SHOULD GET IN THE HABIT OF CHECKING SERVERS AND COMPUTERS FOR UPDATES:
- Designate a person to do this task monthly (for dental clients, we suggest the HIPAA Security Officer).
- Go to each server and workstation, including any laptops in use, and “Check for Updates” even if it says no updates are available. We recommend this be done at the end of the day.
- Apply updates and reboot.
- Check for updates again until you get the message “Your device is up to date.”
- Check updates for any 3rd party software using that software provider’s update instructions.
- Call 3C if there are any computers or servers that won’t update.

